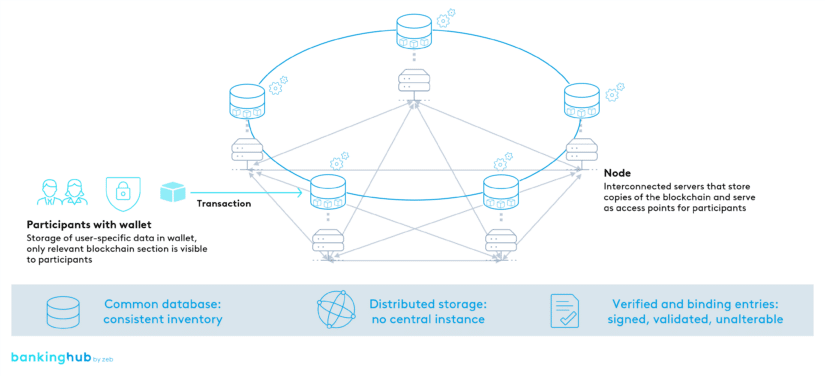
DLT technology using the example of blockchain
The best known DLT application is the blockchain. Blocks represent cryptographically linked database entries that record transactions transparently and tamper-proof.
Nodes, which are access points to a DLT, are an integral part of the network and possess a copy of the entire database, known as the ledger, to validate transactions. This increases trust by mitigating the potential malfunction of a single node.
Continuous data synchronization in the DLT
Transparency: continuous synchronization ensures that each node always has the latest information. This makes DLT a trustworthy and transparent solution for handling data and transactions in digital networks.
Transactions: to ensure verified and binding entries, transactions are signed and verified by nodes using cryptographic methods before being included in a block. This prevents forgery and guarantees that only valid transactions are recorded in the ledger.
Verified and binding DLT entries: Proof of Work, Proof of Stake and Proof of Authority
Consensus: various mechanisms such as Proof of Work (PoW), Proof of Stake (PoS), and Proof of Authority (PoA) are used to achieve consensus on transaction validation and maintain ledger integrity.
- PoW relies on computationally intensive tasks to generate the next block, but this requires significant power consumption.
- PoS, on the other hand, selects the block producer based on the stake of cryptocurrency held, which is more efficient.
- PoA delegates block creation to known and trustworthy nodes, thereby improving speed and scalability.
The choice of consensus mechanism depends on the specific requirements of the DLT network.
To access a DLT, participants typically use a wallet.